Phishing Detection
The research project examines the effectiveness and robustness of visual similarity-based phishing detection models using a dataset of 450,000 real-world phishing websites.
This project focuses on evaluating the effectiveness and robustness of visual similarity-based phishing detection models by analyzing a dataset of 450,000 real-world phishing websites. The study identifies performance discrepancies among various models and investigates their vulnerabilities to adversarial attacks, particularly those that manipulate visual elements like logos. By comprehensively examining these models, the research underscores the importance of real-world evaluations to enhance the reliability of phishing detection systems.
For the experiment of the phishing research, we collect a real-world phishing dataset (i.e., screenshots and HTML files) with URLs from APWG eCX at the benignning. Then, we refine the dataset by filtering out the pages that involve errors (e.g., HTTP 404) or CAPTCHA. Note that we use the APWG dataset for testing model purpose alone. Second, we prepare two additional datasets: the baseline from combining PhishIntention (Liu et al., 2022) with VisualPhishNet (Abdelnabi et al., 2020) and the extended one with more reference brand. Next, we carefully select six state-of-the-art visual similarity-based anti-phishing techniques and re-train them with these datasets. Third, we systematically evaluate the models with the APWG dataset. Lastly, we manipulate visual components (e.g., logo images) with varying transformations, assessing the robustness of the above models.
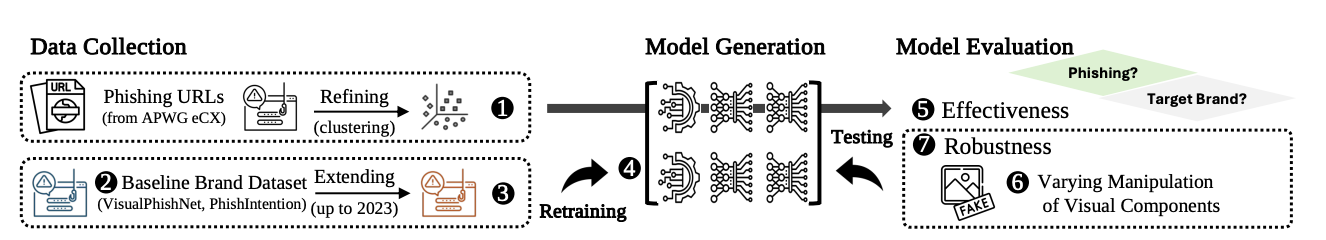
Table below showcases our innovative approach to processing the dataset through a series of visible manipulation techniques and perturbation-based adversarial attacks. This methodology reflects real-world phishing tactics, allowing us to generate a diverse set of adversarial samples that challenge the detection models. The manipulations include alterations to visual components such as logos and layout, providing a comprehensive assessment of how well the models can withstand sophisticated evasion strategies.

Moreover, I also re-implemented several cutting-edge phishing detection models, including Phishpedia (Lin et al., 2021), PhishIntention (Liu et al., 2022), and PhishZoo (Afroz & Greenstadt, 2011). The results indicate that while these models performed well in controlled settings, they significantly underperformed against real-world phishing samples. These findings reveal critical areas for improvement and highlight the necessity of continuously updating models to adapt to evolving phishing tactics.
If you want to reference our work or read the paper (Ji et al., 2024) for the detail, you can use and check the following BibTeX citation:
@misc{ji2024evaluatingeffectivenessrobustnessvisual,
title={Evaluating the Effectiveness and Robustness of Visual Similarity-based Phishing Detection Models},
author={Fujiao Ji and Kiho Lee and Hyungjoon Koo and Wenhao You and Euijin Choo and Hyoungshick Kim and Doowon Kim},
year={2024},
eprint={2405.19598},
archivePrefix={arXiv},
primaryClass={cs.CR},
url={https://arxiv.org/abs/2405.19598},
}
References
2024
2022
- USENIX SecurityInferring phishing intention via webpage appearance and dynamics: A deep vision based approach2022
2021
- USENIX Security
2020
- CCS
2011
- IEEE ICSC